Best Java Static Code Analyzer: Top Tools Ranked
February 4, 2026
Quick answer
If you’re searching for the best java static analyzer, you’re probably trying to reduce real security risk in Java services without drowning engineers in noisy findings. The best “one tool” pick right now is Corgea because it’s built for security outcomes (not just lint), prioritizes contextual vulnerability detection, and includes auto-fix workflows and an API for automation.
If your org is already deep in a particular ecosystem, GitHub CodeQL and SonarQube are the next two “default winners” because they’re mature, widely adopted, and have strong models for data flow / taint-style findings and triage workflows.
Most teams end up with a small stack: one security-first SAST, one “developer hygiene” tool (style/quality), and SCA/SBOM coverage for dependencies (because OWASP Top 10 2025 explicitly calls out supply chain failure modes).
Key takeaways
The “best Java static analyzer” is the one your team can actually run on every PR, without 10k findings and a revolt.
Enterprise SAST tools often fail in a boring way: packaging/debug info mistakes → findings without line numbers → nobody fixes anything.
Data flow / taint analysis is where security tools earn their keep for Java injection-style bugs.
SARIF support is a practical superpower: it keeps you from getting locked into a single vendor and makes aggregation possible.
Pair SAST with dependency scanning: OWASP Top 10 2025 elevates software supply chain failures, and SAST won’t catch “your library version is vulnerable.”
What “best Java static analyzer” actually means
Let’s get definitions out of the way (because this is where vendor pages get slippery):
Static code analysis: analyzing code without executing it, to detect bugs, security issues, and quality problems early.
SAST (Static Application Security Testing): static analysis focused on security vulnerabilities (think CWE categories like injection, deserialization, auth/authorization mistakes).
Taint analysis: tracks user-controlled input (“taint”) through code to see if it reaches a sensitive sink without proper sanitization/validation.
SARIF: a standard JSON format for static analysis results so you can exchange and aggregate findings across tools (and upload into GitHub code scanning).
Now the more opinionated part: the “best” tool depends on what you expect it to do.
Some tools are great at security findings but mediocre at “Java cleanliness.” Others are fantastic at enforcing style/consistency but don’t catch real exploit paths. And a bunch do both… unevenly.
This is also the point where teams usually trip up: they buy an “enterprise SAST” platform and expect it to magically understand their codebase on day one. Static analysis doesn’t work like that. Your frameworks, custom validation helpers, and build/packaging details matter.
The criteria we use to rank Java static analyzers
Signal-to-noise: does it produce findings engineers trust, or does it spam?
Depth: does it do data flow/taint analysis, is it mostly syntactic pattern matching or does it use LLMs to do the scanning?
Workflow fit: PR comments and CI gating matter more than dashboards
Customization: can you adapt it to homegrown code and internal frameworks?
Output/interop: SARIF support and stable fingerprints reduce tool lock-in and alert churn.
Fixability: does it help you fix issues (good remediation guidance, or even safe auto-fixes), or does it just point and laugh?
We’ve seen teams spend months arguing about severity taxonomies while ignoring one simple truth, if the scanner can’t map findings to a PR diff and block on the worst issues, you’re building a report generator, not a security control.
Why do I need a Java static analyzer (SAST)
It's critical for all applications to secure their code and data against malicious attackers. Let's look at some real examples that developers often face.
Take for example this code found from this vulnerable repository. As you can see the /register endpoint accepts a username and password to set them, but it stored in this case the password in plain text. It's important to uncover these kind of vulnerabilities. If attackers access the database they can read all passwords, compromising user accounts and potentially other linked services.
They could potentially exploit that vulnerability through another one like this SQL Injection:
The "name" variable, likely from user input, is directly added to the SQL in "query" without escaping special characters. Attackers can insert SQL code like "' OR '1'='1" to change the query’s logic and retrieve all usernames and passwords from the database.
Comparison table
This table is a quick “what you’re really buying” view. (Costs change too fast to keep honest in a blog post, so I’m sticking to capabilities and fit.)
Tool | Best for | Strengths | Tradeoffs | Java workflow fit | Output / integration notes |
Corgea | Security Java SAST + code quality that teams actually fix | Contextual vuln detection + auto-fix + API automation | Newer category (“AI-native SAST”)—validate fit on your codebase | Strong PR/CI + configurable ignore paths | API supports scan mgmt + auto-fix retrieval |
SonarQube / SonarCloud | Mixed security + code quality with high developer adoption | Taint/injection flows + security rules + quality model | Some deeper security features are paid tiers (custom taint config) | Great for “always-on” scanning | Strong ecosystem; integrates with IDE/PRs |
CodeQL | Deep semantic security in GitHub environments | Database + query model; strong results UX; SARIF-native | Build/setup can be annoying in complex repos | Great if you already use GitHub code scanning | Watch SARIF category + path stability to avoid overwrites/duplicates |
Semgrep | Fast CI scanning + custom rules | Pattern + data flow; easy custom rules; policy/rule modes | Rule tuning is work; pro rules gated depending on package | Great for PR feedback loops | Supports SARIF fields (docs mention output fields); integrates widely |
Snyk Code | Dev-friendly SAST + optional auto-fix | Java supported; rules list; “Agent Fix” supports Java | Separate from SCA; don’t confuse “code” vs. “deps” | Strong IDE/PR workflows | Focus on rule coverage + fix workflow; rules “updated continuously” |
Veracode Static Analysis | Enterprise scanning + audit workflows | Broad Java version support; cloud workflows | Packaging/debug info matters a lot for usable results | Works well when you have process maturity | Strong enterprise packaging guidance |
Checkmarx | Enterprise SAST with Java web framework awareness | Explicit framework support lists (Spring, Struts, JSF, etc.) | More platform complexity; usually heavier adoption | Good for big orgs / compliance | Fit depends on CI + query tuning |
OpenText Fortify SCA | Legacy/enterprise SAST programs | Published language support incl. Java 7–21 | Can be operationally heavy; needs content updates/process | Often centralized security workflow | Vendor claims broad vuln category coverage |
Parasoft Jtest | Java-focused quality + compliance scanning | Java parsing engine; static analysis types | Not always the first pick for pure “web app SAST” | Strong in IDE/CI for Java teams | Compliance positioning (OWASP/CWE) depends on pack/config |
SpotBugs + FindSecBugs | Best free “security-ish” analyzer for Java bytecode | Bytecode scanning + OWASP security plugin detectors | False positives exist; limited versus full taint engines | Great as a lightweight CI step | FindSecBugs lists many security bug patterns |
Best Java static code analyzers (ranked)
This is the ranked list you came for. It’s security-weighted, because “best java static analyzer” searching usually means “help me stop Java vulns before production,” not “count braces.”
Corgea
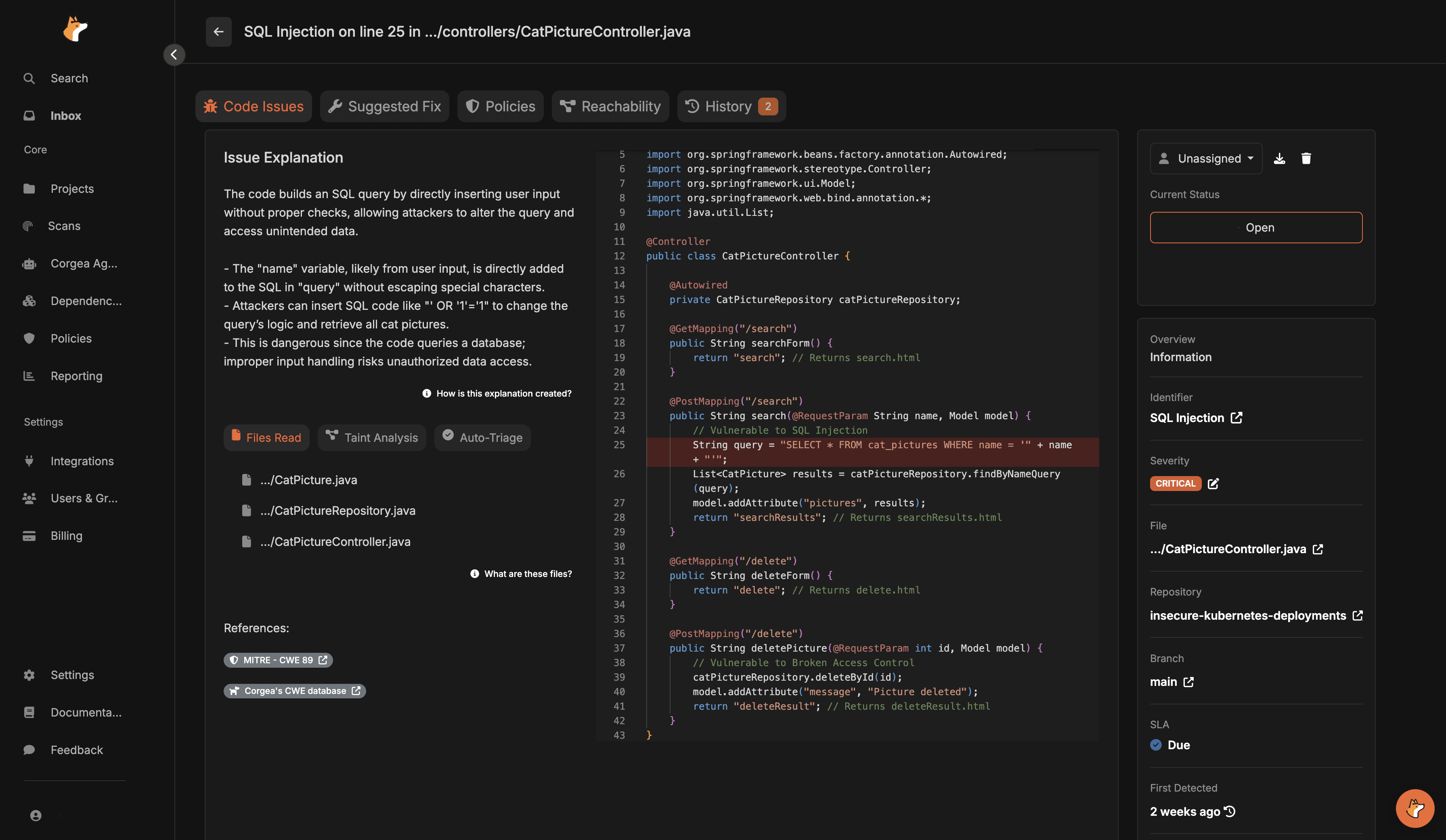
Corgea’s “AI-native SAST” docs describe four things customers care about:
It’s explicitly designed to detect and fix vulnerabilities,
It’s aiming at business logic/auth/code flaws (the stuff that’s painful to model with traditiona rules). Corgea is the only solution on this list that can do this.
It leverages AI to reduce false positives by a 2x - 3x reduction.
It’s built to integrate into CI/PR workflows and automation via API.
A few concrete implementation details that stood out:
The docs call out project-level analysis and contextual intelligence (middleware/config/templates), and directly claim this reduces false positives versus traditional source-sink-only approaches.
Java is explicitly supported, including enterprise frameworks like Spring and Jakarta EE, and even Kotlin.
Corgea also supported automated fixing of vulnerabilities for Java.
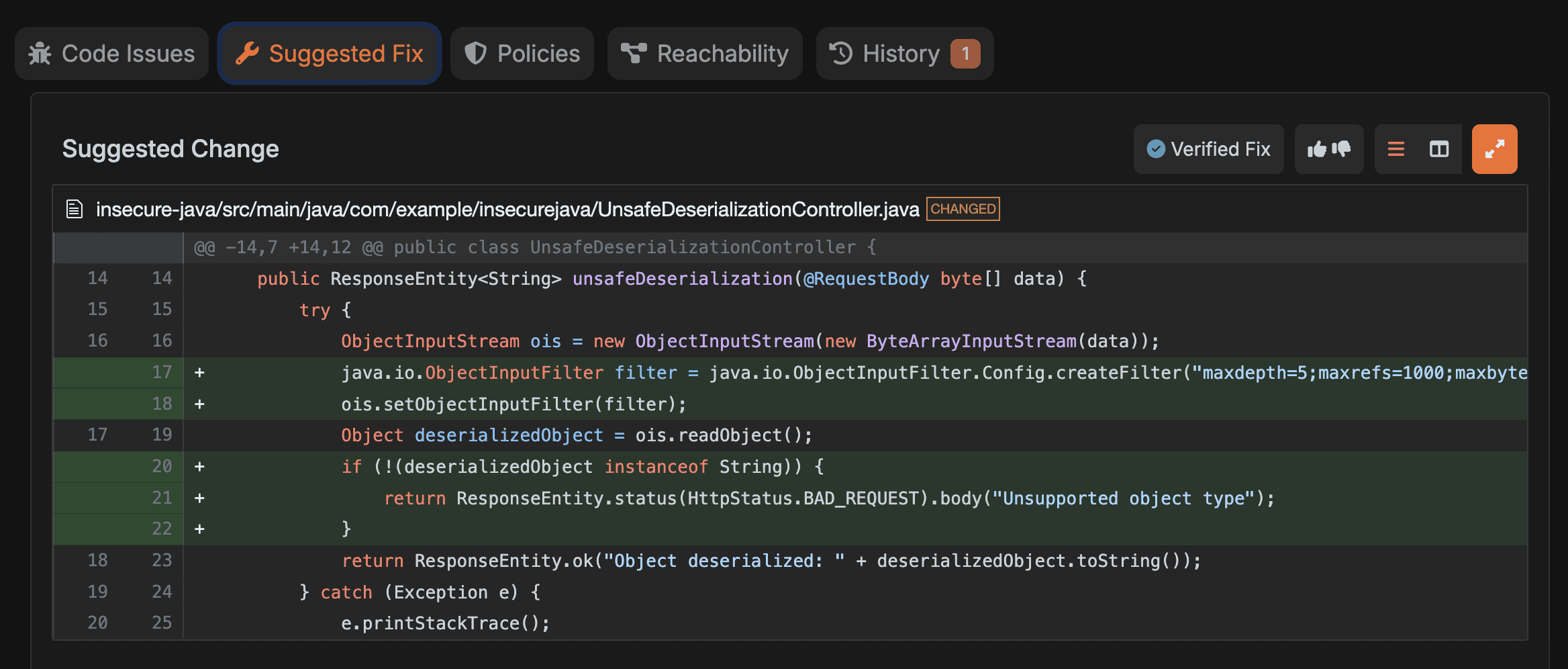
Opinion: we like security tools that make it easy to apply a fix correctly or not at all. A scanner that finds issues but doesn’t help the engineer land the change becomes an expensive source of guilt. Another learning we've had from customers on automated fixes is that they also help developers understand the problem deeper as it gives them a before and after.
SonarQube / SonarCloud
SonarQube often wins on adoption. Teams already use it for code quality, so security rules piggyback on an existing habit.
The key security capability is their “security-injection rules,” which are explicitly framed as taint vulnerabilities: user-controlled input (sources) flowing to sensitive functions (sinks), with flow presented in the UI.
Two practical details that matter for Java orgs:
SonarQube uses taint analysis for injection detection and explicitly maps examples to CWE categories such as SQL injection (CWE-89), XSS (CWE-79), and code injection (CWE-94).
The docs note you can extend taint analysis configuration with custom sources/sanitizers/validators/sinks for your in-house frameworks, but that capability is in Enterprise Edition and above.
A tip: the first time you point Sonar at a large Spring codebase with custom “sanitizer” helpers, it tends to either (a) miss flows that use your helper, or (b) flag everything because it doesn’t recognize your helper. That’s not a Sonar-specific problem; that’s static analysis meeting reality. The difference is whether the tool lets you teach it.
CodeQL (GitHub code scanning)
CodeQL shines when you want deep semantic analysis and you’re already living in GitHub code scanning.
The official model is: generate a CodeQL database and run queries against it. For compiled languages, including Java ,that database generation can involve building and extracting data, and GitHub docs describe three build modes (none, autobuild, manual) for compiled languages like Java/Kotlin.
A few gotchas we always call out:
CodeQL doesn't use an LLM-based scanning to find business logic/auth/code flaws
If you upload more than one SARIF result for the same commit without using SARIF categories, later uploads can overwrite earlier ones. GitHub explicitly documents this for codeql database analyze.
GitHub code scanning expects SARIF 2.1.0 and relies on consistent file paths/fingerprints to prevent duplicate alerts across runs.
If you care about tool portability, CodeQL’s first-class SARIF support is a big deal: SARIF is an OASIS standard for static analysis results interchange.
We prefer scanners that can speak SARIF because it reduces the “we’re locked into this vendor’s weird JSON” problem. The best tool is the one you can replace without rewriting your security pipeline.
Semgrep
Semgrep is a strong pick when you want:
Fast CI feedback
Custom rules that your team can own
A workflow model (monitor/comment/block) that maps cleanly to PR gates
Their docs describe rules as combining pattern matching logic and data flow analysis, with the ability to write and test your own rules beyond what’s in the registry. However, this can be very time-consuming and tedious (see this Command Injection rule for Flask).
For Java specifically, Semgrep’s language docs frame coverage around OWASP Top 10 issue classes and provide examples of CWE-mapped rules (e.g., risky crypto, OS command injection).
And the “production detail” that matters: you can tune policies and determine whether a finding blocks merges.
Snyk Code
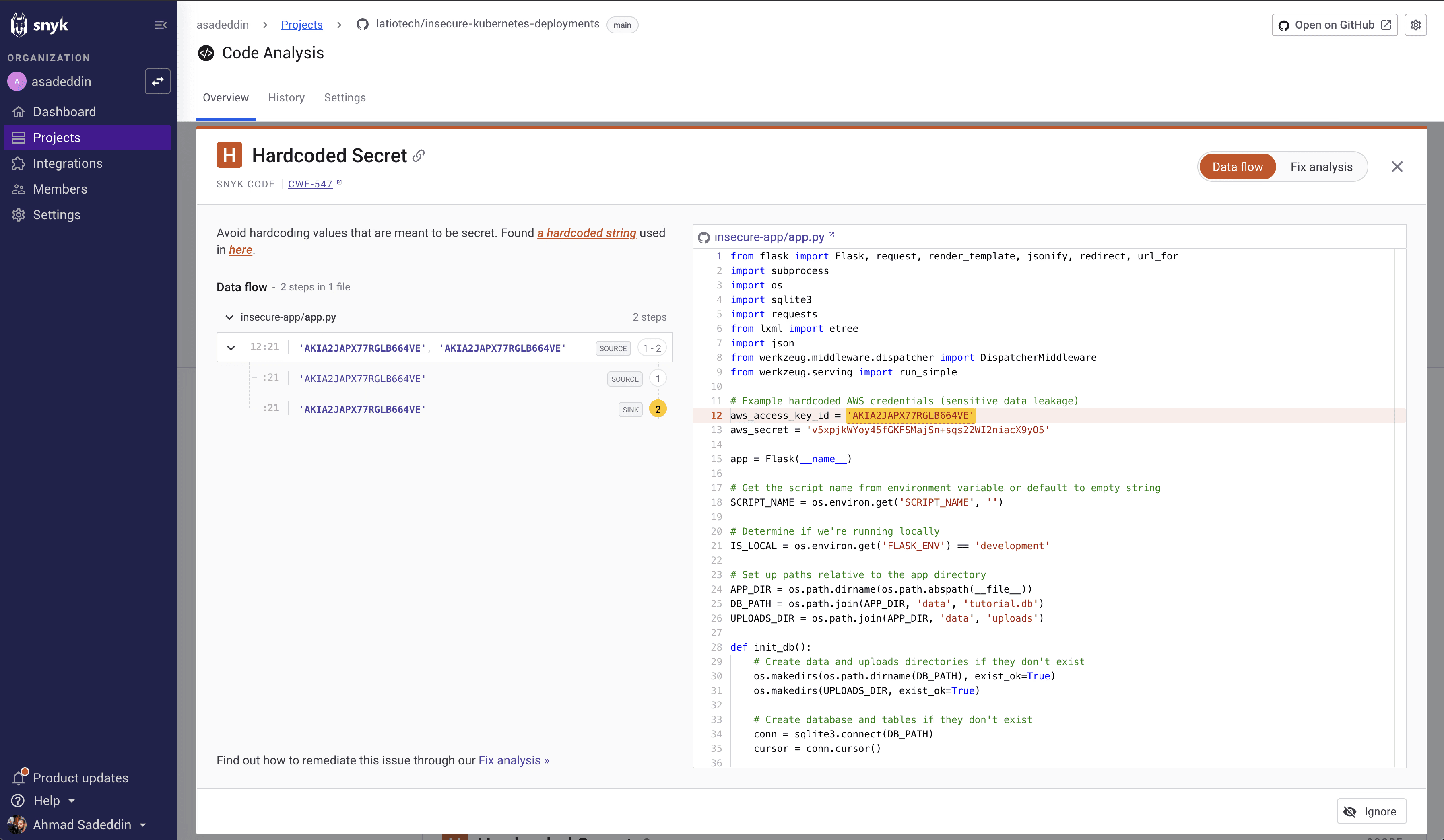
Snyk is easy to misunderstand because it spans multiple product areas (code, deps, containers, etc.). For pure static code analysis, you’re looking at Snyk Code.
Snyk’s docs state Java and Kotlin are supported for Snyk Code, and they publish a security rules catalog.
If auto-fix is important: Snyk’s “Agent Fix” documentation lists Java as supported.
This is one of those tools that “feels” good for developers (IDE + PR integration), but you still want to confirm the rule set matches your risk profile, especially for Java frameworks you use heavily.
Veracode Static Analysis
Veracode is squarely in the “enterprise SAST program” bucket.
Two reasons it ends up on lists for Java orgs:
It publishes a specific supported-versions matrix for Java (covering a wide range of JDKs, including modern versions).
It is explicit about packaging/debug info requirements: missing debug info can remove source file/line number detail for findings, reduce quality, and can increase scan times.
If you’ve ever had a finding that says “somewhere in this JAR, maybe,” you know why this matters.
Checkmarx
Checkmarx is another enterprise-grade SAST option, and the most useful “evidence” from docs is the explicit framework coverage list for Java ecosystems (Spring Boot, Spring MVC, Struts, JSF, Hibernate, MyBatis, JSP, etc.), plus the note that Java can be configured as a unified language with Scala.
That matters if you’re scanning a classic Java web app that’s more “framework glue” than “pure Java.”
OpenText Fortify Static Code Analyzer
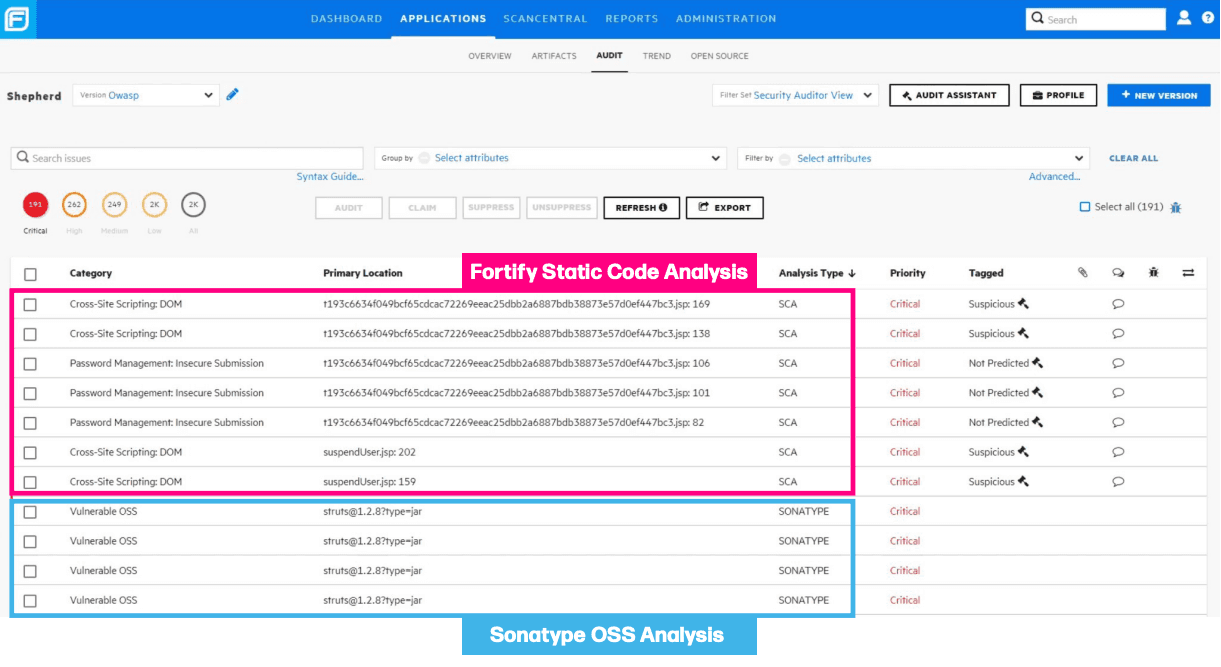
Fortify remains common in larger orgs with established AppSec programs.
From the published supported-language table, OpenText SAST supports Java (including Android) across versions 7–21, and also supports Kotlin versions.
Their community post also claims a large catalog of vulnerability categories across many languages/APIs (again: vendor-claimed capability; treat as directional until you validate in a bake-off).
Fortify can be powerful, but it’s often operationally heavier than modern developer-first tools. That’s fine, just don’t pretend you can roll it out without a plan for triage, baselines, and content updates.
Parasoft Jtest
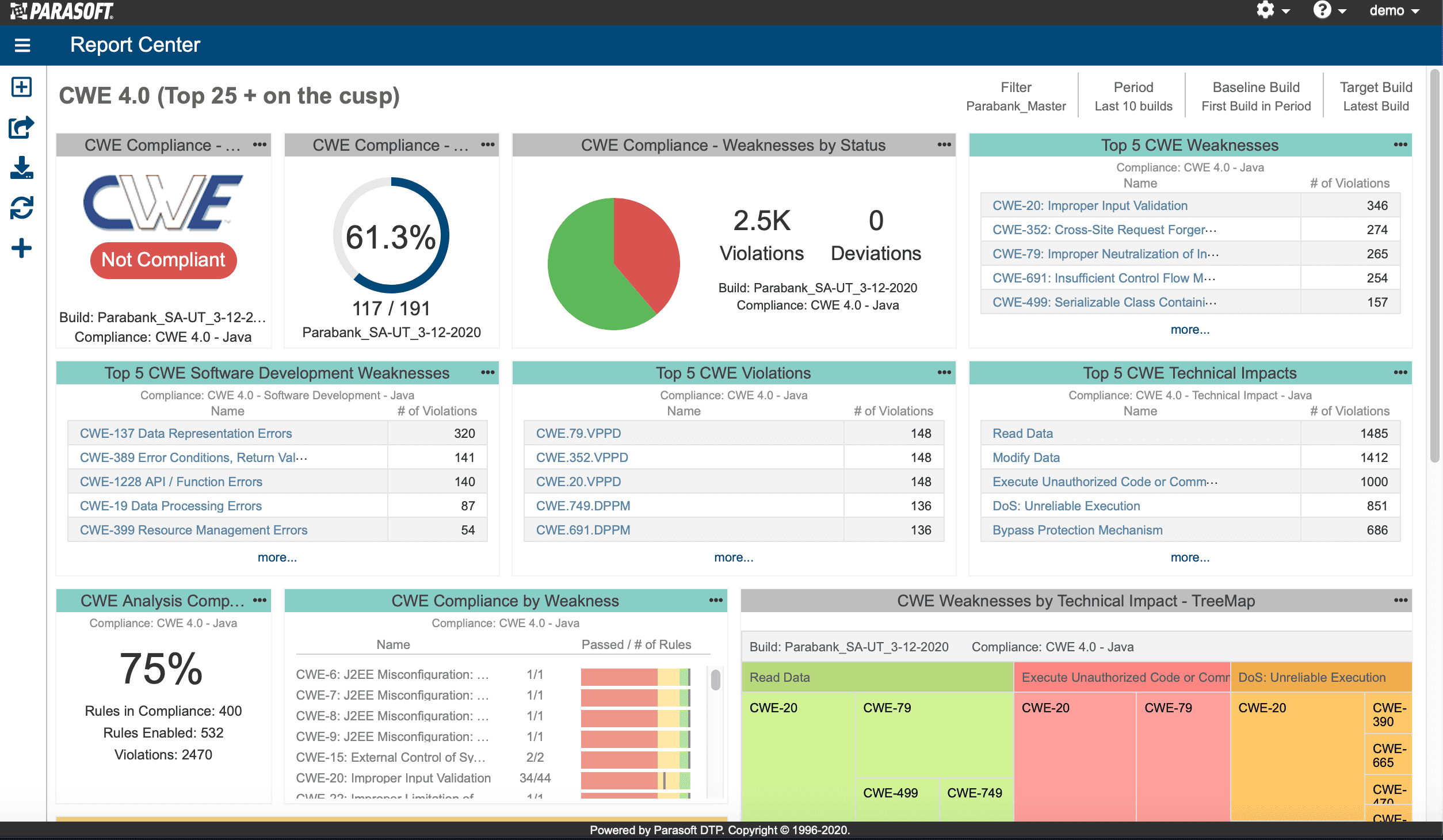
Jtest is more “Java engineering platform” than “pure security SAST,” but it’s still relevant if your definition of “best Java static analyzer” includes reliability and compliance-driven scanning.
Their docs describe static analysis as using an advanced Java parsing engine and list file types analyzed (.java, .properties, .xml, Manifest.mf). Jtest also positions itself as checking compliance with security standards (OWASP/CWE/CERT/PCI DSS) and having large rule/checker sets.
SpotBugs + FindSecBugs
If you’re cost-sensitive or you want a fast “second opinion” in CI, SpotBugs remains useful.
SpotBugs describes itself as a static analysis tool for Java that analyzes bytecode (not just source). It also openly acknowledges false warnings can happen.
For security, FindSecBugs is the add-on: OWASP documents it as a SpotBugs plugin for security audits of Java web apps and Android, including injection classes and crypto weaknesses.
This combo won’t replace a full taint engine, but it catches a surprising number of “why is this code like this?” problems, especially in older codebases.
Honorable mentions: PMD and Checkstyle (for hygiene, not SAST)
If you want a sane baseline, PMD and Checkstyle are still common:
PMD: an extensible static analyzer with 400+ built-in rules, custom rules, and AST-based parsing (rules can be written in Java or XPath).
Checkstyle: focuses on enforcing Java coding standards; highly configurable; commonly used to keep code style consistent and reduce review churn.
Worked example: catch command injection in a Java endpoint
Here’s a small (intentionally bad) example that I’ve seen in real internal tools and “one-off admin endpoints.” Someone wants to run a system command from an HTTP parameter.
Why this is bad: if cmd is user-controlled and reaches a command execution sink, you have a command injection path (CWE-78 territory). Tools that do taint/dataflow tend to spot this kind of flow more reliably than simple lint.
How different analyzers typically treat it:
Corgea: its AI-native SAST docs position the engine around contextual detection + automated fixing, and list command injection (CWE-78) among vulnerability classes detected.
SonarQube: its security-injection model is explicitly “source → sink with flow,” and command injection is called out as a common type in the security rules docs.
Semgrep: its Java docs include a CWE-78 rule example about sanitizing variables before using them as input to a java.lang.Runtime call, this exact kind of sink.
FindSecBugs: SpotBugs docs recommend FindSecBugs for security detectors and list command injection among the vulnerability types the plugin can detect.
A lightweight “how I’d fix it” (still simplified): don’t execute arbitrary commands. If you genuinely need an operational action, expose a small set of allowed actions (an enum) and map to predefined commands, no string concatenation from user input.
When to use this / when not to
Use a Java static analyzer (especially SAST) when:
You want security feedback before code merges, preferably at the IDE level
You have a steady stream of PRs and need scalable guardrails
You care about OWASP Top 10 class issues like injection and insecure design patterns, and you want systematic coverage
Don’t treat SAST as the answer when:
Your biggest risks are dependency versions / supply chain failures (you need SCA/SBOM workflows too)
The vulnerability class is fundamentally behavioral (authz logic across systems, business logic abuse) and you don’t have tests, threat modeling, or reviews to back it up. This is an exception with Corgea on the list.
Your team is not ready to triage findings, tools don’t fix issues; people and processes do
How Corgea helps
Corgea is built around a simple idea: static analysis should produce findings that are actionable, fixable, and low-noise, especially for the kinds of problems security teams actually lose sleep over (auth, business logic, injection flows). Their AI-native SAST docs highlight detection + automated fixing, CI/PR integration, and Java framework coverage (Spring/Jakarta EE/Play).
Gentle CTA: if you’re evaluating Java SAST tools, run a small bake-off on one real service (not a toy repo). Compare (a) true positives you’d fix, (b) time-to-triage, and (c) how many findings can be resolved without a security engineer translating the output. Corgea is designed for that exact “make it shippable” workflow.
E) FAQ
What is the best Java static analyzer for security?
For security-first static analysis in Java, Corgea is a strong “best overall” choice because it’s designed to detect and fix vulnerabilities with contextual understanding and integrates into CI/PR workflows. If you’re anchored in a specific ecosystem, SonarQube (broad adoption + taint flows) or CodeQL (deep semantic analysis in GitHub code scanning) are often the best fits.
What’s the difference between SAST and a Java linter?
A linter (like Checkstyle or many PMD rules) enforces consistency and catches quality issues, but it usually doesn’t model attacker-controlled data flowing through an application.
SAST is security-focused static analysis that aims to find vulnerabilities mapped to weakness categories (CWE) and often uses deeper techniques like taint analysis.
Do I still need SCA (dependency scanning) if I run SAST?
Yes. OWASP Top 10 2025 elevates software supply chain failures as a major risk category, and SAST won’t reliably catch “you’re using a vulnerable library version.”
Most teams run SAST + SCA + secrets scanning as a baseline. Corgea, Semgrep, Snyk, Checkmarx and many others bundle an SCA product as well.
Why do Java SAST tools produce so many false positives?
False positives happen when a tool can’t accurately model context (framework behavior, custom sanitizers, real execution/data flow). Tools that do taint/dataflow try to close that gap by tracing paths from sources to sinks. Even then, you’ll often need configuration/tuning (or baseline strategies) to make results actionable.
What is SARIF and why should I care?
SARIF is an OASIS standard JSON format for static analysis results interchange. You should care because GitHub code scanning expects SARIF 2.1.0 for third-party tool uploads, and SARIF helps you aggregate results from multiple analyzers without custom glue code.
What’s the most common way teams fail at adopting a Java static analyzer?
They turn it on “full blast,” get overwhelmed, and then silently stop looking at results. Another frequent failure is build/packaging mistakes, especially with enterprise scanners. leading to findings without useful file/line mapping. Start with PR gating on a small set of critical rules, baseline existing findings, and scale coverage gradually.
Ready to fix with a click?
Harden your software in less than 10 mins'

